Why OT Cyber Security is Critical: 3 Benefits of a Security Fabric
Operational Technology (OT) is hardware and software that detects or causes changes by directly monitoring and controlling industrial equipments, assets, processes, and events. It incorporates a comprehensive range of programmable systems or devices interacting with the physical environment.
Why is Operational Technology(OT) Cyber Security Important?
As industrial systems become more correlated, they also become more visible to vulnerabilities. The high cost of industrial machinery and the devastation to communities and markets that an attack could cause are key constituents for companies looking to preserve their industrial networks. Add legacy equipment, safety regulations that may prevent any changes being made to equipment, and compliance laws that require raw data to be made available to third parties, and you have quite a hurdle on your hands.
The best report is that it is feasible to warrant industrial networks without disturbing operations or risk non-compliance. By using solutions that allow complete clarity of network control traffic and securing the right security policies, you can put an efficient OT strategy in place that will protect your processes, people, and profit and significantly lessen security vulnerabilities and incidents.
The convergence of operational technology (OT) and information technology (IT) affects the safety of industrial control systems (ICS) and supervisory control and data acquisition (SCADA) systems. Connecting a previously air-gapped (not connected to the outside world) OT network to the internet via an IT network immediately exposes the OT network and all connected OT devices to the entire threat landscape and become targets for hackers interested in terrorism, cyber warfare, and espionage. Expanding well above the conventional factory plant floor, raids on critical infrastructures such as power plants, factories, water treatment systems, oil rigs, and traffic control systems can result in dangers to national security, economical loss, the threat to brand reputation, and even loss of life.
Recently, ATS announced that it has achieved Operational Technology (OT) Specialization as part of the Fortinet Engage Partner Program (read more about this milestone here) and has published a comprehensive article about OT Cybersecurity.
For over a decade, Fortinet has protected OT environments in critical infrastructure sectors such as energy, defence, manufacturing, food, and transportation. Organizations have an efficient, non-disruptive way to ensure that the OT environment is protected and compliant by planning security into intricate infrastructure via the Fortinet Security Fabric.
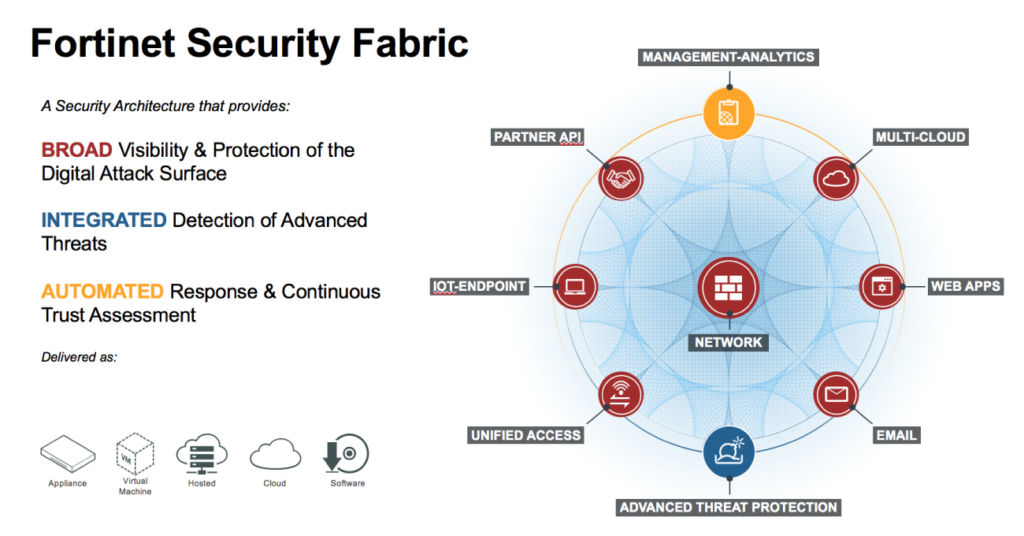
The Fortinet Security Fabric
The Fortinet Security Fabric is the industry’s highest-performing cybersecurity medium, powered by FortiOS, with a rich open ecosystem. It spans the expanded digital attack surface and process, allowing self-healing security and networking to protect devices, information, and applications. The Security Fabric is Created on Three Key Features:
Broad – Reduce risk and control the complete digital attack surface
A broad portfolio allows combined threat detection and policy enforcement across the complete cyber attack surface and lifecycle with combined networking and security across edges, clouds, endpoints, and users.
Integrated – Close the security gaps and lower the complexity
Combining security, operations, and performance across various technologies, locations, and deployments allow entire visibility. It also strengthens all form factors’ security, comprising hardware assets, virtual machines, cloud-delivered, and X-as-a-Service.Fabric-ready Partner products are included in the Fabric environment.
Automated – Faster time to prevention and efficient operations
A context-aware, self-recover network and security posture leveraged cloud-scale and developed AI, provides near-real-time automatic, user-to-application blended protection across the Fabric.
3 Benefits of a Security Fabric
Ensuring merged OT-IT networks with a security fabric helps security leaders reach the required visibility, control, and behavioral analytics they need. Since OT assets and IIOT assets typically depend on conventional security, the network must be secured to confirm cyber threats do not gain access to these devices. To execute consistently effective IT and OT security, a security fabric delivers:
Visibility
Find any device connected anywhere on the IT-OT network, define the degree of trust, and constantly monitor behavior to keep a level of trust. Describe the attack surface and secure active device and traffic profiling. Traffic visibility confirms actionable intelligence, and OT security teams can dictate permitted traffic, ports, protocols, applications, and services. Enforcement topics within the environment confirm north-south and east-west security.
Control
Relying on each OT system and subsystem to do its work—and only its work, multifactor authentication secures the relevant people have the appropriate set permissions and access. Network segmentation and micro-segmentation deliver a layered and balanced approach with control zones. Sandboxing detects threats on the OT network, and automated quarantine controls them from harm.
Continuous Monitoring
Ongoing analysis of behaviors in OT web networks enables teams to learn what, where, when, who, and how by collecting intelligence about familiar and unfamiliar threats. A central security tool assists with logging, reporting and analytics, and assesses activity accumulated across the system. It also delivers security information and event management, and security orchestration automation and response abilities. OT security insights are achieved via user and device behavior analysis and threats assessments to guarantee constant protection.
ATS: Leading OT Cyber Security Provider in the UAE
ATS is a top choice with over 18 years of experience as a trusted OT cyber security provider. ATS is one of the leading OT cyber security providers in the UAE and Middle East region, with over 400+ projects implemented in the country and other parts of the Middle East.
Today, ATS is delighted to share with you a compilation of essential information, methodologies and terminologies in a comprehensive eBook about OT Cyber Security entitled “ATS Operational Technology (OT) Cyber Security eBook”. Learn more about OT cyber security in this new eBook from ATS, and watch out for our next ATS Coffee Break Session about the ATS OT Cyber Security eBook this coming January 2022.


















