SECURITY THROUGH VISIBILITY: HOW TO STRENGTHEN YOUR IOT SECURITY WITH ATS
Some bit of good news in the field of cybersecurity at last – compared to last year’s hectic activity in malware targeting large enterprises and critical infrastructure sites, Q2 of 2021 presented relative calm.
Redoubled efforts to protect industrial operation after the tumultuous 2020, with increases in industry-wide regulations, investigation efforts by law enforcement, and progresses made by cybersecurity solution experts have all delivered significant results. For example: compared to last year’s Q2, a significant drop of almost 40% has been recorded when it comes to DDoS attacks, as stated by Kaspersky.
However, this does not mean the state of cybersecurity of large enterprises and critical infrastructure sites is anywhere near stable.
IOT BOTNETS ON THE RISE
While reports agree that Q2 2021 provided a respite from busy cybercriminal activities in the year’s first quarter, it has also been noticed that malicious agents have been actively seeking out new ways of attack distribution and deployment, looking for ways to amplify their effect, with this particularly evident in the field of DDoS.
An example of this would be the latest news of the discovery of Meris, a new massive IoT botnet abused for DDoS attacks.
Mēris (the name of the botnet coming from the Latvian word for “plague”) is made up of around 250,000 malware-infected devices and has already broken records in terms of largest volumetric DDoS attack.
In a typical case of DDoS ransomware strategy, the group behind Mēris extorts large enterprises by threatening to shut down crucial servers to those who can’t afford such interventions. So far, the actors behind Mēris have targeted companies in the United States, Russia, and New Zealand, with the size of the company representing no issue to this botnet due to its high request-per-second (RPS) power. The latest news of Mēris activities report an attack taking place on September 5th, hitting a volumetric milestone of 21.8 million RPS.
Developments of IoT botnets such as this, along with the dramatic rise in ransomware activities overall in the past quarter, paint a worrying vision for the months to come.
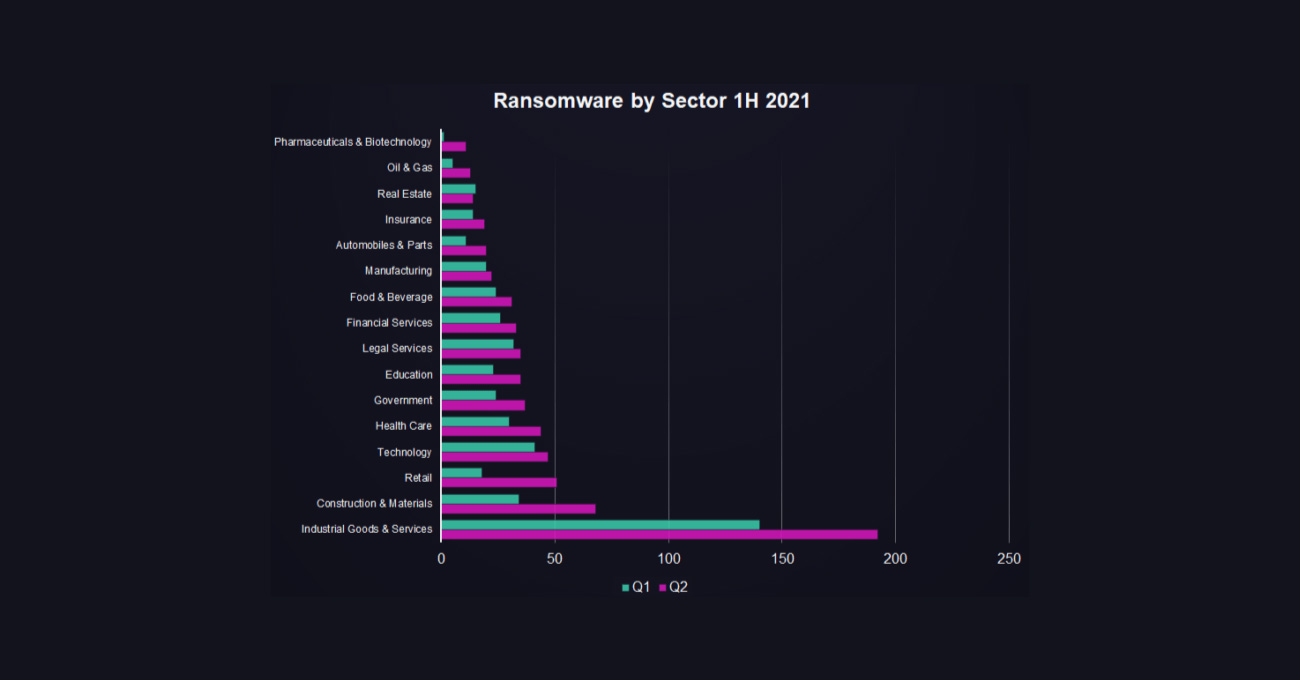
Ransomware groups who made their marks in the last months of 2020 and spring of 2021 have either temporarily paused their operation, or exited the market – but others are coming up to take their place. According to Digital Shadows, increases in the numbers of ransomware attacks can be found in every sector, and Industrial Goods and Services are taking the brunt of the hits in particular.
With all this in mind, it becomes clear the short-lived rest from widespread cyberattacks on business-critical systems should not serve as a reason to pause the development of your protection plans, but instead to work towards tightening your security even further.
In today’s article, we’ll look at the 3 best ways to increase the level of your IoT security.
1. SECURITY THROUGH VISIBILITY
Be it when working on adapting to a next-step technological development or just operating an existing enterprise-level network system, it is easy to get lost in the process and focus on productivity over protection. What naturally follows suit is that securing your industrial tech environment comes as an afterthought.
Architecting a security solution, however, should actually be a part of your enterprise from day one.
With protective procedures becoming an integral part of your IT and OT, administrators can freely operate within these networks without worrying about data being misplaced – or assets being overlooked.
Performing asset inventory and then maintaining its visibility presents a daunting task for many industrial environment professionals. Some of the challenges of conducting an inventory come from older equipment not being designed to communicate with network probes; adding onto that, most executives worry that asset inventory is impossible to achieve without halting critical operation.
However, not having real time visibility into the way your operations are being conducted on a day to day basis presents a very real safety liability: if critical assets fall into disuse, with their levels of monitoring decreasing, they become possible entry points for malicious agents.
This is why it is of critical importance to have your security monitoring system account for each and every asset onsite, as well as provide an overview of network data migrations and pathways – in order to quickly spot unusual activity or uninvited guests.
2. HIGH LEVEL OF AUTOMATION
Our second point is closely related to the first.
Humans may be well-developed, highly-evolved machines – but we too make mistakes, and often. In fact, some researchers claim that an average person makes three to six errors during a single working hour.
These errors may be something small and insignificant, like a typo in the subject line of an email. However, there’s also a significant margin of error in security monitoring – disregarding unusual device activity at first and assigning it to a small, unexpected malfunction opens the door for larger breaches down the road. This, of course, carries detrimental ramifications for your entire operating ecosystem.
In order to decrease chances of human error to their absolute minimum, highly-automated security solutions are recommended. Products such as Cisco Cyber Vision, for example, not only track process anomalies, asset modifications and variable changes, but function as fully automated, live threat intelligence that notifies security personnel of both asset vulnerabilities and intrusions.
Choosing a solution which automates your security process not only adds an additional, error-free layer of protection but also allows your staff to be that much more confident in their daily work.

3. NETWORK SEGMENTATION AND USER ACCESS CONTROLS
At the heart of network security, lies the question of who has access to which network segments, and what freedoms they are allowed within their access.
Some of the most frequent IoT breaches and takeovers happen due to insecure password systems – one of the top security issues for IoT devices.
One example would be Mozi, a peer-to-peer botnet that exploited, among other things, weak IoT device passwords in order to take over and launch DDoS attacks, steal data and execute commands.
While the arrest of Mozi’s alleged deployer earlier this year might bring its own operations to a halt, there is nothing to prevent other interested parties to model their own botnets according to Mozi and other similar services that came before it (such as Mirai and Reaper).
There exist a multitude of solutions to circumnavigate the potential problem of IoT device password breach – most experts recommend resetting default usernames and passwords. But that should just be the first step – there are ways to further secure your IoT, such as password expiration dates and account lock-out options in case of unverified activity.
Overall, the best way to approach this issue would be a comprehensive access management plan that extends across your entire network – which would, in case a breach does occur, be able to minimize the damage via network segmentation.
Simple additional strategies, such as implementations of necessary two-factor and multi-factor authentication can also go a surprisingly long way when looking to secure your IoT from unauthorized access.

















