NCA Urges Organizations in KSA to Embrace Operational Technology Cybersecurity Controls (OTCC) for Enhanced OT Cybersecurity
The National Cybersecurity Authority (NCA) of Saudi Arabia has released a set of Operational Technology Cybersecurity Controls (OTCC-1:2022) as part of its efforts to regulate and safeguard the country’s cyberspace. This initiative is aligned with the Kingdom’s Vision 2030, which emphasizes the importance of cybersecurity.
The NCA developed these controls after conducting a comprehensive study of various national and international cybersecurity frameworks and standards. They also incorporated guidance, standards, and controls from international sources focused on operational technology (OT) and industrial control systems (ICS) cybersecurity.
The primary objective of these controls is to enhance the cybersecurity of OT systems within the Kingdom by establishing minimum requirements for organizations to protect their cyber-physical systems. By implementing these controls, organizations can defend against cyber threats that have the potential to cause detrimental impacts which could cause serious impacts on critical infrastructures.
These controls serve as an extension of the NCA’s existing Essential Cybersecurity Controls (ECC) and demonstrate the authority’s commitment to promoting cybersecurity and resilience in Saudi Arabia’s critical infrastructure and industrial sectors and addressing the main cybersecurity pillars: strategy, people, process, and technology.

As leading experts in OT/ICS cybersecurity, we provide comprehensive solutions and services to effectively address cybersecurity concerns. Our platforms enable organizations to achieve compliance with the OTCC-1:2022 cybersecurity controls. Leveraging the power of ATS and Cyberwise platforms, organizations can significantly enhance their cybersecurity posture and ensure robust protection for their OT and ICS environments.
Strategic Insights into OTCC Methodology, Mapping, and Optimizing Cybersecurity Controls for Operational Technology
The OTCC Methodology and Mapping Annex, an integral part of the OTCC document, was created by NCA. It encompasses various components, including the design principles and methodology of the OTCC, the correlation between OTCC and ECC Domain 5, connections to numerous international standards and best practices, the methodology employed in the design of OTCC’s main domains and subdomains, as well as the approach for defining the levels of OTCC Controls and Sub-Controls.
The Operational Technology Cybersecurity Controls (OTCC-1:2022) are designed to be implemented in Industrial Control Systems (ICS) located in critical facilities owned or operated by both government organizations and private sector entities responsible for Critical National Infrastructures (CNIs), regardless of their location within or outside the Kingdom of Saudi Arabia. This represents a unique perspective within OTCC that encompasses all types of industrial sites.
To ensure ongoing compliance with OTCC-1:2022, all organizations to which it applies are required to implement all necessary measures, as outlined in Article 10, item 3 of the NCA’s mandate, and in accordance with Royal Decree number 57231, dated 10/11/1439AH.x”
All organizations falling within the defined scope and possessing or operating ICS technologies are required to adhere to the relevant controls specified in OTCC-1:2022. However, organizations must ensure that implementing these controls will not compromise the uninterrupted operation of their own systems and services. It is crucial to strike a balance between compliance with the controls and maintaining the continuity of the organization’s essential operations. To achieve this, asset owners, vendors, and subject matter experts need to collaborate to develop and execute a feasible action plans.
Meanwhile, NCA issued tools for assessment and compliance and facility level identification, to organize the process of the evaluation and compliance measurement against the OTCC controls, and to organize the process of assigning the appropriate levels to the critical facility within the scope. As NCA will periodically review and update the OTCC as per the cybersecurity requirements and related industry updates.

Compliance with Essential Cybersecurity Controls (ECC 1:2018) is a mandatory prerequisite for the organization.
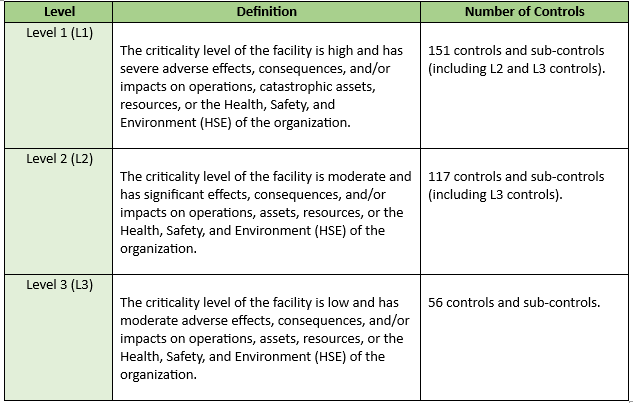
The Operational Technology Cybersecurity Controls (OTCC) are categorized into three levels of criteria, which consider the criticality, consequences, and impact on the organization’s business operations and service availability. Additionally, the assessment includes evaluating the potential negative impact on the health, safety, and environment (HSE) of the organization. Furthermore, the assessment also takes into account the potential adverse effects on the national economy, national security, or social influence. These criteria help in effectively evaluating the significance and implications of the OTCC controls.
Control levels based on the outcome of the facility-level identification tool:
To comply with the requirements, the NCA proposes enhancing the level of baseline protection provided to OT systems. This involves investing in ongoing security improvements, reassessing risk management strategies to align them with evolving cyber threats, broadening the range of fundamental security controls, and identifying security vulnerabilities to proactively address them and enhance the overall security posture. One of the most crucial aspects here is the adoption of a proven OT security perspective and a risk-based approach in industrial environments, rather than relying on traditional IT security viewpoints.
The industrial cybersecurity experts at ATS and Cyberwise are ready to assist you in creating a comprehensive plan to adhere to OTCC-1:2022 and enhance your risk management practices for effective threat containment and mitigation. Reach out to our experts today to commence your journey toward conducting a thorough threat assessment and implementing effective mitigation strategies.


