ICS/OT CYBER SECURITY FUNDAMENTALS: 5 REASONS TO PROTECT YOUR COMPANY
Implementing an effective and comprehensive operational technology (OT) cybersecurity strategy is more crucial than ever before.
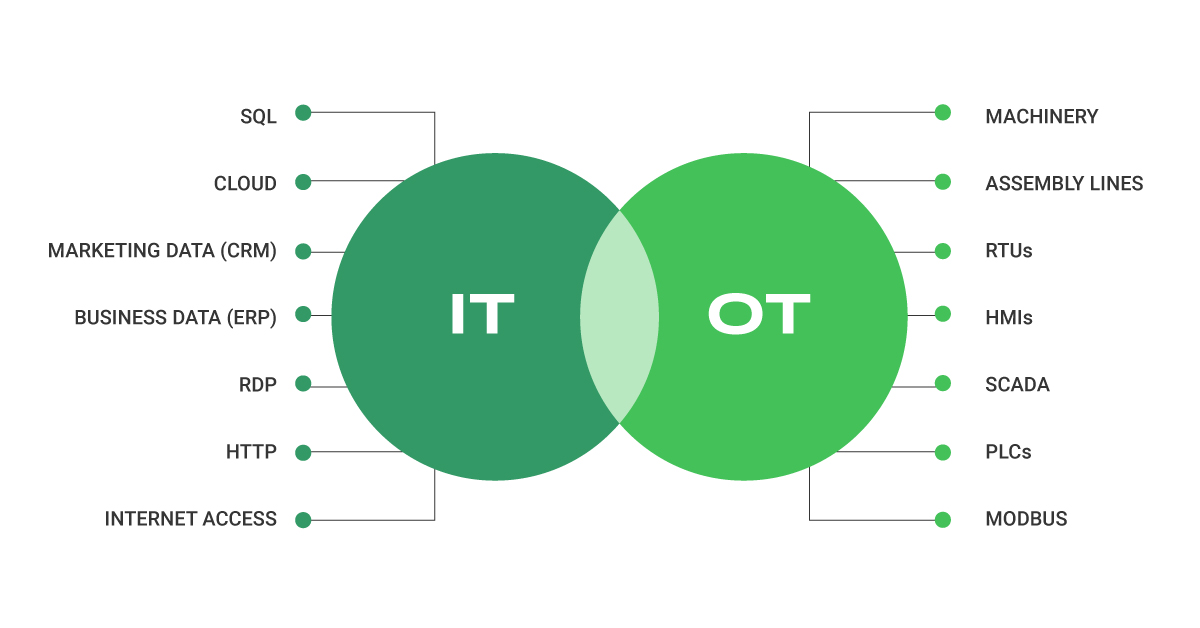
Most companies have long been implementing thorough IT security measures to protect their data and digital assets, but it wasn’t always the case for OT environments. With the growth of the Industrial Internet of Things (IIoT) and the convergence of IT and OT as companies seek improved connectivity through the internet and enterprise technologies, the risk for malicious cyberattacks became increasingly pertinent in OT environments.
A survey by Fortinet found that 90% of organizations experienced at least one OT system intrusion in 2020. Where IT cyber attacks have a number of consequences relating to reputation and customer trust, OT cyberattacks can have disastrous consequences in the physical world. It’s critical that businesses keep their reputation, assets, and processes protected with robust cyber threat management.
Companies need to mitigate a host of risks stemming from online warehouse systems, cloud-connected machinery, and IoT devices in use across workstations. So why exactly is it so important to protect OT from cybersecurity challenges?
In this article, we’re sharing 5 reasons to protect your company with OT cybersecurity.
WHAT IS OT CYBERSECURITY?
Operational technology (OT) cybersecurity refers to the software and hardware used to protect operational technology critical infrastructure, personnel, and data.
OT includes technologies that we use in the physical world. It includes:
- Industrial Control Systems (ICS)
- Supervisory Control and Data Acquisition (SCADA)
- Distributed Control Systems (DCS)
In the past, OT cybersecurity wasn’t mission-critical because OT systems weren’t connected to the internet and therefore weren’t at risk from outside threats. However, with the expansion of digital innovation initiatives and the convergence of IT and OT networks, companies must protect their connected ICS/OT devices.
Data collection and analysis practices are becoming increasingly important in business operations. This, along with the convergence of IT and OT is facilitating “big data” initiatives, makes it essential for businesses to reassess their cybersecurity strategy to protect their OT environments.
The purpose of IT-OT convergence is to provide organizations with a unified view of their industrial systems while using process management solutions to facilitate the delivery of accurate information to employees, machines, sensors, and devices.
5 REASONS TO PROTECT YOUR COMPANY WITH OT CYBERSECURITY
OT environments are desirable threats for cybercriminals looking to access information, disrupt operations, or cause environmental damage or contamination. Attacks like the TRITON attack on a chemical facility located in the Middle East, plus the Ukrainian electrical grid attacks and the most recent Colonial Pipeline cyberattack in the US, illustrate the damage that can be caused when OT environments come under threat.
A 2019 CyberX report found that 40% of industrial sites have at least one internet connection on-site, and 84% of them have at least one remotely accessible device. As the connectivity of OT environments increases, so does the risk of coming under attack from clever hackers. OT networks control critical processes and infrastructure meaning network failures can have more disastrous consequences than in IT systems.
1. INCREASED CONNECTIVITY OF INDUSTRIAL IOT (IIOT)
IoT devices have become commonplace in OT environments like oil and gas, electricity, and mining sectors digitizing their operations. This led to the birth of the Industrial Internet of Things (IIoT) which includes interconnected sensors, instruments, and other devices that share the same network as computer industrial applications. Global IIoT platform spending is projected to reach 12.44 billion in 2024, achieving a 40% CAGR since 2018.
There are numerous benefits of IIoT within OT environments. One study by Gartner found that 80% of organizations that have adopted IIoT are achieving “better than expected results.” These devices can help to:
- Streamline operations
- Lower costs
- Increase efficiency
- Improve inventory management
- Enable industrial operations to access real-time data and analytics and cross-site connectivity.
IT trends and technological innovations born from digital transformation have a huge effect on ICS/OT environments. Despite the obvious advantages that stem from improved connectivity in a digital world, IIoT devices bring a new set of security risks for organizations.
These cybersecurity challenges include a lack of security awareness, outdated software, unsatisfactory hardware integrity, and fragmented security solutions that don’t work in the ICS/OT environment. Other issues can arise due to IoT technologies not being built into security models within the OT environment.
2. INDUSTRIAL CYBERATTACKS CAN CAUSE DAMAGE IN THE PHYSICAL WORLD
As mentioned previously, ICS and OT environments have traditionally existed separately from a company’s IT systems. The growth of data analytics, the assimilation of cloud computing, and the proliferation of other types of automation systems have caused the convergence of IT and OT environments. For this reason, ICS vulnerabilities have increased and are further exacerbated by the shift towards remote work as IT and OT become inseparable.
Because ICS/OT environments connect the digital and physical world, the potential for attackers to cause physical damage to an organization’s infrastructure is increased. There are many examples of high-profile cyberattacks on ICS systems that have caused physical damage to organizations. For instance, compromised remote site attacks on SCADA systems can cause interruptions to the movement of assets or more sophisticated consequences like the manipulation of pipeline equipment.
Potential consequences might include:
- Expensive production outages
- Safety failures
- Manipulation of or damage to equipment
- Physical injury or loss of life
- Environmental damage
- The devastation to communities and economies
These physical consequences can interrupt facility operations, cause damage to equipment, or potentially endanger on-site employees. Due to the interconnected nature of critical sectors, cyber-physical malfunctions and disruptions can set in motion a domino effect and have a more damaging, lasting impact.
3. OT INFRASTRUCTURE ASSETS ARE EASY TARGETS
Another reason to protect OT environments is the fact that they’re often considered easy targets for seasoned attackers. Many ICS and SCADA systems include new technology but rely on legacy systems and aging hardware with unpatched software configurations. This renders these systems vulnerable to attacks. Patching OT systems often require vendor approval and testing before they can be applied, meaning the process is slow and results in downtime.
OT cyberattacks are becoming increasingly common and cybercriminals are developing malware specifically designed to attack critical infrastructure (e.g. Stuxnet). It’s more important than ever for companies to identify vulnerabilities in their OT environment and put in place the appropriate measures to mitigate cyber risks.
4. OT CLOUD SECURITY THREATS ARE GROWING
In the ICS sector, cloud security solutions quickly gain traction because they can be scaled without delay to respond to business needs. They’re typically available under cost-effective pay-as-you-go models and can enhance efficiency within data-intensive industries such as manufacturing. However, introducing cloud computing into the OT environment poses its own set of challenges.
Cloud-based solutions are offered by third-party providers, meaning asset owners are granted limited control over the security infrastructures and data access control. This makes organizations vulnerable to OT cloud security threats like siloed communication between local production and cloud components as a result of DDoS attacks. Organizations must protect their data with the right procedures, policies, and training to ensure the data they have stored in the cloud remains secure to avoid potential attacks.
5. PEOPLE ARE STILL THE WEAKEST LINK IN CYBERSECURITY
People pose the main challenge for organizations when it comes to ICS/OT cybersecurity. Lack of training and employee awareness is often the cause of cyberattacks occurring. Unlike IT cybersecurity practices, employees dealing with ICS or SCADA systems might not be as aware of the threat cyberattacks pose to OT environments and the potential consequences.
Securing your ICS/OT environments against the threat of cyberattacks is a process that should include thorough training and planning. A good place to start is by introducing cybersecurity into existing planning exercises. Instead of separating physical and digital worlds, quantify the risks of cyberattacks holistically and emphasize the threats that they pose to your organization’s critical infrastructure. It’s also worth communicating in simple language to translate IT security risks into the ICS/OT environment and increase awareness.
MOVING FORWARD WITH OT
With the convergence of IT/OT environments, securing industrial organizations requires an integrated approach that accounts for the whole sphere of digital security (IT, OT, IIoT, and more). Organizations need to put in place the right people, systems, and processes to protect their assets and mitigate the risks of cyberattacks.
To do this, organizations must bridge the gap between OT and IT to find solutions. Implementing firewalls and VPN security measures, training employees to be constantly vigilant, and outlining response plans can help organizations understand, identify, and protect against security attacks in OT environments.

















