ATS Knowledge Sharing Series: What is Operational Technology (OT)?
Operational Technology (OT) is hardware and software that detects or produces changes by directly monitoring and controlling physical devices, processes, and events. It incorporates a comprehensive range of programmable systems or devices interacting with the physical environment.
OT is standard in Industrial Control Systems (ICS) such as a SCADA System. In the world of critical infrastructure, OT is used to control systems, building management systems, transportation systems, physical access control systems, physical environment monitoring systems, and physical environment measurement systems.
Cybersecurity risk management is essential to ensure the secure and trustworthy delivery of the goods and services provided and supported by OT. The NIST OT Security Program comprises multiple collaborative projects across the NIST Information Technology Laboratory and Communications Technology Laboratory. As this technology rises and unites with networked tech, the demand for OT security advances exponentially.
Threats to OT(operational technology) systems vary from malware to attack to data theft or data manipulation, with serious outcomes. Industrial Control Systems (ICS), SCADA, and such a comprehensive category of systems are commonly known as OT (Operational Technology) systems. OT Security means executing security controls around these systems.
The consequence of crimes to OT Security is felt on Personnel Safety, Availability of critical manufacturing processes, loss of data integrity, data confidentiality, and data theft, especially of IP (Intellectual property).
Therefore, the threats regularly trying to breach these controls need to be observed and controlled on a 24X7 basis from an OT-SOC (Operational Technology Security Operations Center).
A brief history about OT security:
The demand for industrial controls began with the first Industrial Revolution of the 1700s. Converting steam into usable energy was tough and critical; it took decades to develop a governor that could truly manage the steam engine output’s speed to tame this new power source. Each next industrial revolution (we are currently into the fourth) has started or was started by further advancements in controls on physical systems.
Programmable Logic Controllers:
The programmable logic controller (PLC) was first designed in 1971 to replace traditional relay stacks. PLCs implemented electronics to production automation for the first time, thereby driving the third Industrial Revolution. The discovery of the PLC made building and remodeling control logic much easier. It soon became the base for simple but powerful control loop systems, consisting of a sensor, controller (e.g., PLC), and actuator.
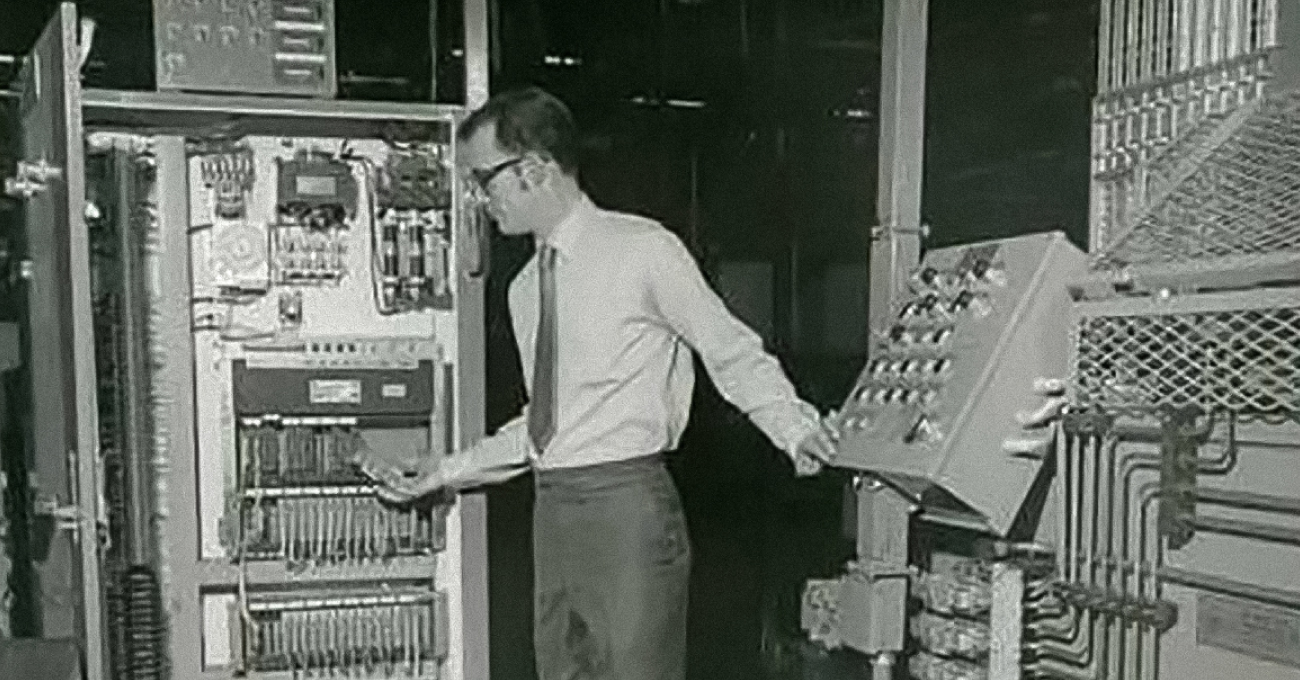
Control Systems:
Very complex behavior can be modeled and managed with nested and cascading architectures from these simple process loops. The logic can be built to control constant manufacturing processes, such as those found in a factory or chemical plant, and batch manufacturing processes, such as observed on an assembly line. Control systems also found their way into classified applications such as electrical power grids, railways, and pipelines.
Supervisory Control and Data Acquisition (SCADA) Systems:
Often, data acquisition is as necessary as the control in distribution system applications. Traditionally, Supervisory Control and Data Acquisition (SCADA) systems are used to blend data acquisition systems (sensors) with data presentation solutions and data transmission systems. It supports HumanMachine Interface (HMI) software, creating centralized clarity into an entire system, such as an electric grid.

Distributed Control Systems (DCS):
Distributed Control Systems (DCS) provide a related set of functionalities as SCADA but on the factory system, typically with less complexity, or at least diversity, in networking and communications channels.
Industrial Control Systems (ICS) and Operational Technology (OT):
All of the technologies we have reviewed have traditionally been followed up under the title of industrial control systems (ICS). However, in contradistinction to IT, the term operational technology (OT) has become trendy in recent years.
Why is Operational Technology (OT) security important?
As industrial systems become more correlated, they also become more visible to vulnerabilities. The high cost of industrial machinery and the devastation to communities and markets that an attack could cause are key constituents for companies looking to preserve their industrial networks. Add legacy equipment, safety regulations that may prevent any changes being made to equipment, and compliance laws that require raw data to be made available to third parties, and you have quite a hurdle on your hands.
The best report is that it is feasible to warrant industrial networks without disturbing operations or risk non-compliance. By using solutions that allow complete clarity of network control traffic and securing the right security policies, you can put an efficient OT strategy in place that will protect your processes, people, and profit and significantly lessen security vulnerabilities and incidents.
What is the difference between IT (Information Technology) and OT (Operational Technology)?
Operational technology systems use many similar tools as IT environments but are created to be applied in different ways. Instead of operating essentially as a tool for the human, OT devices mostly communicate with other machines, such as industrial control systems (ICS). Their goal is to ensure that the ICS assets operate correctly and meet these devices’ high availability and uptime demands.
IT-OT Convergence
For several years, industrial systems depended upon established protocols and software manually operated and controlled by people and had no link to the outside world. For this cause, they were a reasonably insignificant target for hackers as there was no networked interface to attack and nothing to gain or damage. The only way to infiltrate these systems was to get real access to a terminal, and this was no simple task. OT and IT combined little and did not deal with the same kinds of vulnerabilities.
Today, it’s a very diverse story as we see more industrial systems brought online to give big data and intelligent analytics and embrace new abilities and efficiencies through technological integrations. IT-OT convergence gives companies a single view of industrial systems and process management solutions that ensure that the correct data is delivered to people, machines, switches, sensors, and devices at the right time and in the fittest format. When IT and OT systems work together, new capabilities are discovered, systems can be remotely controlled and operated, and businesses can realize the same security benefits of administrative IT systems.
This shift from closed to open systems has produced a slew of new security risks that need to be addressed.
Perks of IT/OT convergence
The overall perks of IT/OT convergence are cost-effective, better performer, and have better potency. It leads to optimizations and conversions across the company, from operations to business.
Effective Costing
IT-OT convergence assists companies in reducing operating costs by optimizing resource utilization, energy, cooling, and device management. There are fewer systems to obtain and manage by sharing infrastructure, and more effective systems replace legacy infrastructure. It can also lead to savings in the data center, and real estate as single-function devices can be incorporated into blended systems and free up valuable space.
Better performance
Connecting IT and OT data means companies can produce more reliable and significant KPIs. KPIs help drive effectiveness and more powerful performance across the company, assisting both teams in pursuing and achieving mutual goals. It increases clarity into both areas companywide, giving the rest of the company a view into how technology benefits achieve mutual objectives.
Advanced flexibility
Access to real-time data and KPIs empowers companies to respond more promptly to market changes. They can change production timelines based on external factors efficiently while still fitting business objectives. Convergence optimizes workflows and reduces redundant ones, enabling the company to operate more efficiently.
Enhance operational standards
Some businesses use the IT/OT convergence project to bring longstanding IT best methods to their operational systems. For example, they incorporate a patch management program to OT devices to guarantee that they’re working with the latest firmware. Existing IT monitoring technologies can be stretched to OT systems and devices, allowing real-time monitoring and centralized asset tracking. Multiple functions can be consolidated into one monitoring system or console for quicker user experiences to streamline predictive maintenance tasks.
Improved security orchestration
Converged OT/IT systems can join the gap between cybersecurity and physical security for businesses with centralized monitoring systems and appliances. That’s because IT and OT systems have diverse security requirements and capabilities that normally can’t be met with one approach or tool. IT/OT convergence projects improve OT security clarity across the business and help IT teams include existing systems into an overall cybersecurity tactic.

What is the future of OT security?
The worldwide operational technology (OT) security market is highly profitable and predicted to observe notable growth at a strong 8.17% CAGR over the projection period (2018- 2026), shown by the Market Research Future (MRFR) report. Operational technology security is used in different industries to scale, view, and control processes. It is defined as a solution that can assist in detecting or causing a shift in asset-centric companies via direct monitoring and managing events, processes, and physical devices. The security services connected with such systems can help companies evaluate, design, and control activities and security plan to protect OT systems. Such systems are interlinked networks and infrastructures that maintain and control industrial processes.
Want to learn more about OT Security and how it can be implemented for your critical infrastructure? Our ATS experts can guide you through the process of implementing a solid OT Security Plan. Book a consultation now with our experts and watch out for our upcoming eBook on Operation Technology coming this December 2021.


















